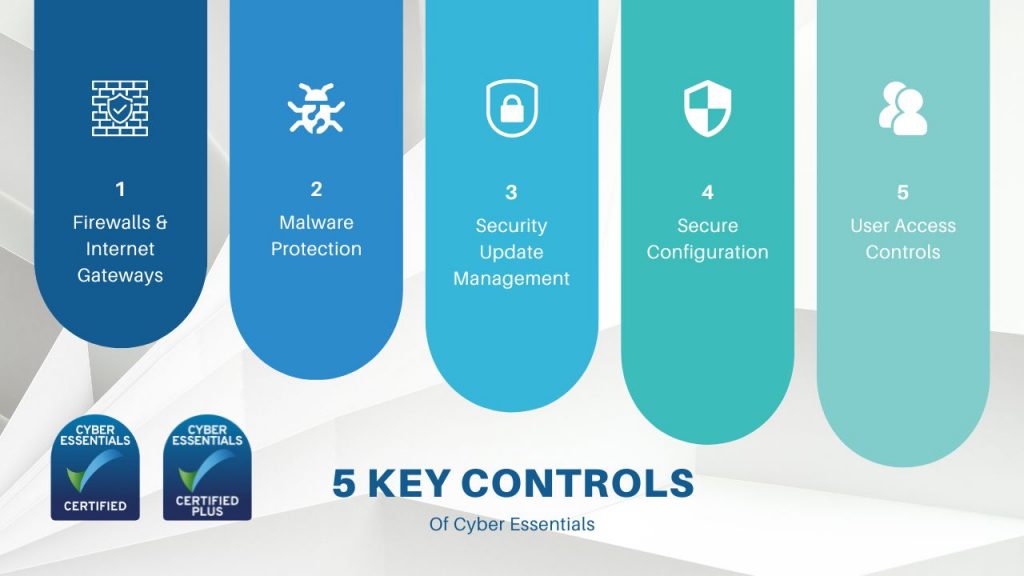
The Cyber Essentials scheme covers 5 key controls. The controls are the backbone of the Cyber Essentials scheme. When implemented correctly, they can significantly reduce an organisation’s vulnerability to the most common cyber threats.
The 5 key controls of Cyber Essentials are:
-
- Firewalls and Internet Gateways
-
- User Access Controls
-
- Security Update Management
-
- Malware Protection
-
- Secure Configuration
While the specifics might vary, the principles behind the 5 Key Controls of Cyber Essentials are relevant to all businesses, large or small. In an increasingly digital world, cybersecurity should be a top priority for all organisations.
Table of Contents
ToggleImplementing Cyber Essentials Key Controls
Implementation can vary depending on the size and nature of your business. However, general measures include setting up systems securely, configuring firewalls properly, controlling access to systems, implementing robust malware protection measures, and regularly applying software patches and updates.
Firewalls and Internet Gateways
As part of the 5 key controls of Cyber Essentials certification, these two elements are seen as one. Boundary firewalls and internet gateways are your business’s first line of defence against Cyber Security attacks.
For the Cyber Essentials certification, setting up and maintaining boundary firewalls and internet gateways effectively is crucial. The certification process examines how these are implemented within your organisation, verifying if they are appropriately configured to provide optimum protection.

What are Firewalls and Internet Gateways?
A firewall is a network security system that monitors and controls incoming and outgoing network traffic. It is a barrier between a trusted internal network and untrusted external networks like the internet.
On the other hand, an internet gateway serves as a door to the internet, controlling data that can pass into and out of a network. When properly configured, it can be a crucial tool in preventing unauthorised access to a network.
Together, these two elements can significantly reduce the potential for successful cyber-attacks, making them essential components of the Cyber Essentials scheme.
Configuring Boundary Firewalls and Internet Gateways
Configuration of boundary firewalls and internet gateways involves defining ‘rules’ that dictate what traffic can and can’t enter your network. This can be as simple as blocking all traffic from suspicious IP addresses or more complex, such as allowing certain types of traffic during specific times of the day.
Configuration should be done based on the ‘least privilege’ principle—only allowing traffic explicitly needed for your business operations. Anything not permitted should be blocked by default.
Maintenance and Monitoring of Firewalls and Gateways
Whilst not a physical product, there’s still a need for regular maintenance of firewalls and gateways to ensure they remain effective. With the opportunity of threats emerging at any time, your defences must evolve accordingly.
Part of the Cyber Essentials scheme involves demonstrating a commitment to regular maintenance and monitoring of your firewalls and gateways. This section of the 5 key controls means applying software updates, patching known vulnerabilities, and regularly reviewing configuration rules to ensure they are still appropriate and effective.
Boundary Firewalls and Internet Gateways Checklist
For Cyber Essentials accreditation, your business must prove it’s effective at blocking high-risk traffic. Unnecessary ports must be closed, whilst all port openings must follow a process and be documented. There are plenty of other protocols under this key control for Cyber Essentials, you can find a copy of the checklist in the Cyber Essentials: An Ultimate Guide to Certification book here.
Remember, achieving the Cyber Essentials certification is not just about ticking the box but building a robust, long-term defence against cyber threats. As such, your boundary firewalls and internet gateways should not be seen as a standalone solution but as one part of a comprehensive cybersecurity strategy.
Ultimately, the strength of your boundary firewalls and internet gateways is directly proportional to the effort you put into their configuration, maintenance, and monitoring. In the fight against cyber threats, they are your first line of defence and, therefore, a critical component of the Cyber Essentials questionnaire.

Your Cyber Essentials Guide & Checklist
Download our FREE Cyber Essentials Guide & Checklist to help you through Cyber Essentials certification.

Secure Configuration
Secure configuration is one of the 5 Key Controls in the Cyber Essentials Certification. This measure ensures systems are set up correctly, mitigating potential vulnerabilities and fortifying your systems against cyber threats.
What is Secure Configuration?
Secure configuration is the digital equivalent of locking your front door and windows before you leave the house. It’s a set of safety precautions we put in place when setting up computers and other devices that connect to the internet, aiming to prevent any potential online threats. As burglars look for homes with unlocked doors, cybercriminals scout for devices with lax security settings to exploit.

Why Secure Configuration is Important for Cyber Essentials
The importance of Secure Configuration in the Cyber Essentials Certification lies in its focus on eliminating unnecessary system weaknesses. When systems are not securely configured, cybercriminals can easily exploit them. This configuration forms the bedrock of your organisation’s cybersecurity and is critical in the certification process.
Secure Configuration Checklist
For the Cyber Essentials certification, secure configuration implies disabling unnecessary software, services, and settings in systems and software. It involves:
Disabling Default Settings: Many systems come with default configurations that may not align with secure practices. This includes open ports, default usernames and passwords, or enabled optional components. Disabling such settings makes systems less susceptible to attacks.
Software Removal: Part of secure configuration involves identifying and removing unnecessary software applications. Unused or outdated software can contain vulnerabilities that provide easy access points for malicious actors.
Limiting User Privileges: To minimise the risk of inside attacks or mistakes leading to data breaches, user access and privileges should be tightly controlled. Users should be given only those privileges which they require to perform their tasks.
Regular Audits: Regular audits are crucial to maintaining secure configurations. These audits ensure that systems remain secure over time, even as changes are made and new threats emerge.

FREE Cyber Essentials Checklist
Download our FREE Cyber Essentials Guide & Checklist to help you through Cyber Essentials certification.

Malware Protection
Malware protection is a critical pillar within the 5 Key Controls of the Cyber Essentials scheme. It ensures that your organisation’s systems are safeguarded from malicious software, which can lead to data breaches, system damage, and even financial loss.
What is Malware?
Malware protection is a critical pillar within the 5 Key Controls of the Cyber Essentials scheme. It ensures that your organisation’s systems are safeguarded from malicious software, which can lead to data breaches, system damage, and even financial loss.
Why Malware Protection is a key part of Cyber Essentials
Demonstrating effective malware protection is paramount for Cyber Essentials certification. It verifies that your organisation can handle common malware threats, showcasing your commitment to cybersecurity. Without robust malware protection, your organisation’s systems could be left vulnerable to attacks, causing technical damage and damaging your organisation’s reputation.

Malware Protection Checklist
The implementation of Malware Protection for the Cyber Essentials Certification involves several strategies:
Antivirus Software: Antivirus software is essential in detecting and removing malware. The software should be kept updated to counter the latest threats effectively.
Regular Scanning: Regularly scanning your systems for malware can help identify and remove threats before they can cause significant damage.
User Education: Users should be educated on the malware risks and how to avoid common pitfalls, such as clicking on suspicious links or downloading unverified software.
Email and Web Browser Settings: Emails and web browsing are common avenues for malware. Adjusting settings to block untrusted email attachments or to show the full URL of web pages can help users avoid malicious content.
Update and Patch Management: Regularly updating and patching software can fix vulnerabilities that malware could exploit.
Malware Protection is critical in the Cyber Essentials Certification. It’s about building a robust and proactive defence against cyber threats, helping to safeguard your organisation’s systems and data. Robust malware protection not only contributes to the overall cybersecurity of your organisation but also takes you one step closer to obtaining the Cyber Essentials Certification.
User Access Controls
User Access Control, a crucial part of the 5 Key Controls of the Cyber Essentials Certification, dictates who can access specific data and systems within your organisation. It’s essential in reducing the risk of internal and external threats.
What are User Access Controls?
At its core, User Access Control is about limiting access to your IT systems to only those who need it to perform their jobs. It’s like a security check at an event, where only people with the right pass can enter.
Why User Access Controls is vital for Cyber Essentials Certification
User Access Control is vital in the Cyber Essentials Certification as it directly impacts your organisation’s vulnerability to internal and external attacks. Poorly managed access controls can allow malicious insiders or compromised accounts to cause significant damage.
User Access Control Checklist for Cyber Essentials Assessment
Successful implementation of User Access Control involves several vital strategies:
Implementing Least Privilege: Users should only be given access to the data and systems needed for their specific roles. This is known as the principle of least privilege.
Strong Password Policies: Enforcing solid and unique passwords can prevent unauthorised users from guessing or cracking passwords.
Multi-factor Authentication (MFA): MFA (also known as two-factor authentication/2FA) adds a layer of security by requiring users to provide two forms of identification before accessing the system.
Regular Audits: Regularly reviewing who has access to what data can help identify potential risks and ensure that only the necessary access is provided.
As your organisation grows, so should your access control strategies. Regularly reviewing and updating your access controls and educating your staff about the importance of data security can help your organisation stay one step ahead of potential threats.
User Access Control is a fundamental component of the Cyber Essentials Certification. By effectively managing who has access to your systems and data, you can significantly reduce the risk of a data breach and move closer towards achieving certification in Cyber Essentials.
Security Update Management
As a pivotal part of the 5 Key Controls of the Cyber Essentials Certification, Security Update Management, also known as Patch Management, ensures that all your software and systems are up to date, helping to defend your organisation against potential cyber threats.
What is Security Update Management?
Security Update Management regularly updates and patches all systems and software in use within your organisation. These updates often contain security improvements that fix vulnerabilities, closing doors that cybercriminals could otherwise use to gain unauthorised access.

Security Update Management for the Cyber Essentials Scheme
The Cyber Essentials Certification places significant emphasis on key controls, Security Update Management. Why? Because one of the easiest ways for cybercriminals to infiltrate your systems is through known vulnerabilities in outdated software. You can drastically reduce your exposure to such risks by keeping all your systems up to date.
Cyber Essentials Checklist: Security Update Management
Implementation of Security Update Management key controls involves several critical practices:
Regular Updates: All systems and software should be updated regularly. This includes operating systems, applications, and firmware on devices.
Automatic Updates: Updates should be set to happen automatically to ensure they are not overlooked.
Timely Patching: When vulnerabilities are discovered, software providers will typically issue patches to fix them. It is crucial to apply these patches promptly to protect your systems from being exploited.
Asset Inventory: Having a detailed inventory of all IT assets in your organisation can help ensure that every system is included during the update process.
The world of Cyber Security moves quickly, and threats are constantly evolving. Therefore, your approach to Security Update Management should also be dynamic, adapting to new threats and vulnerabilities as they emerge. Reviewing and refining your practices helps maintain the effectiveness of your updates and keeps your systems secure.
Security Update Management is a crucial aspect of the Cyber Essentials key controls. Ensuring all your systems and software are kept updated can significantly enhance your organisation’s cybersecurity, protect against cyber threats, and move one step closer to completing the Cyber Essentials scheme.

FREE Cyber Essentials Checklist
Download our FREE Cyber Essentials Guide & Checklist to help you through Cyber Essentials certification.

Key Controls for Cyber Essentials
The 5 Key Controls of Cyber Essentials serve as an invaluable guide for businesses striving to protect themselves from the ever-increasing cyber threats they face. By implementing these controls, businesses can enhance their cybersecurity, safeguard their data, and maintain the trust of their customers. These five essential controls will remain fundamental to a robust cybersecurity strategy and are a requirement for gaining Cyber Essentials accreditation.
Contact us today if you’re looking for assistance with your Cyber Essentials, Cyber Essentials Plus, or Cyber Essentials as a service.
Submit a form below and a Cyber Security Expert will be in touch.
Digital Marketing Lead at Excellence IT.
Writing about Cyber Essentials, Cyber Security and IT Support.
